Same Old Actor From Past
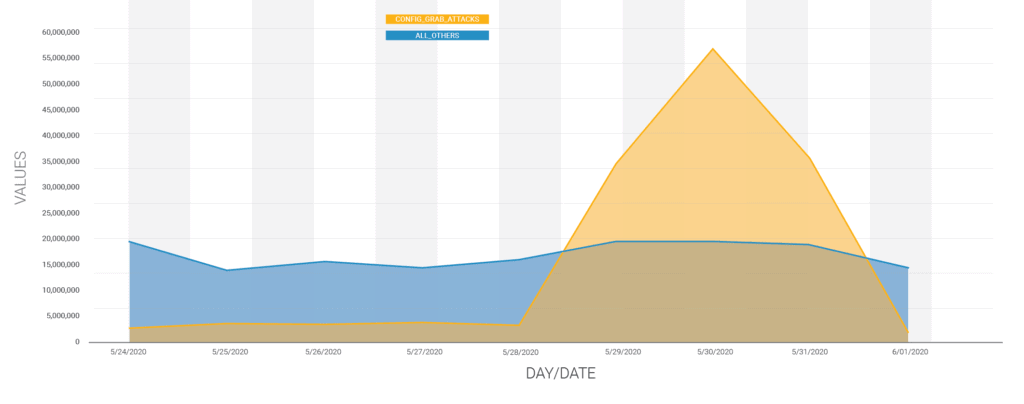
Exploiting any WordPress related vulnerabilities can garner something big. And since the fact is widely accepted, a group that previously exploited XSS cross-scripting vulnerability in WordPress has no targeted old vulnerabilities in unpatched plug-ins, and download configuration files from sites. This, in return, to steal the login credentials of the site’s database. Wordfence reports that this campaign happened last weekend, between May 29th and May 31st, where May 30th has seen a peak number of attacks. It claims to have blocked over 130 million attacks against 1.3 million sites and says there are more unrecorded attacks that might have happened. It further links the author behind it to be the same who’ve leveraged the cross-scripting vulnerability earlier, as most of the IP addresses in this campaign are the same from the first campaign. And here, stealing the credentials could give the attacker access to the site’s database, where he can add/remove users and manipulate content.
Checking and Safeguarding
Wordfence has also depicted the indicators of comprise, where a potential user who thinks if being attacked, can look up into his server logs. And if you find any log entry that contains wp-config.php in the query string that returned a 200 response code, you’re done. It’s advised to change the database password and authentication unique keys immediately. Source: Wordfence