The Upgraded Malware
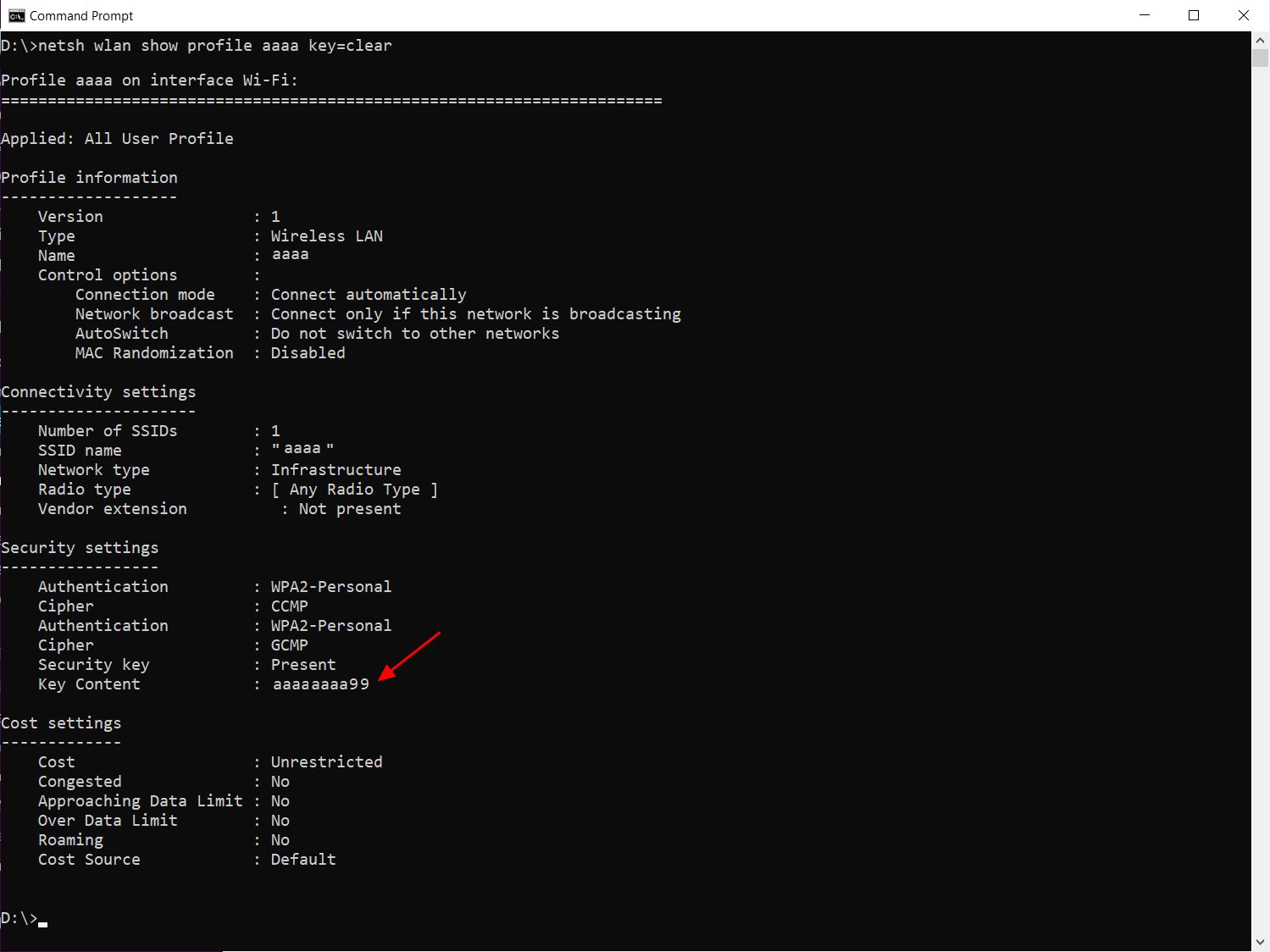
Attackers have long been developing malware that is both hard to be found, and capture as much as data possible from the victim. Now, a malware trojan called Agent Tesla that has been active since 2014, came up with an added feature as Wi-Fi credentials capturer. This new module was found by the Malwarebytes team, which has assessed the highly obfuscated code of Agent Tesla recently. After passing through a phishing attack and infecting the desired user, Agent Tesla would perform its purpose of collecting all the system data and transport to the hacker. The stolen data includes the PC’s FTP clients, file downloaders, browsers, system’s username, CPU architecture, RAM, OS version, etc. Alongside this, it would also collect the Wi-Fi credentials too. Researchers found the malware, after finding the nearby wireless network profiles, it would first issue a netsh command adding to the SSID and a key=clear argument. This would scrape the Wi-Fi names and their passwords in a plaintext format. Collecting those details would enable a hacker to set a stage for future attacks as DDoS, where the entire network is used for targeting a particular service. To avoid this from happening, experts suggest users be conscious about opening any suspicious documents from email, replying to them or clicking any links within. These would contain executable malware that self-install and run in the background without users’ knowledge and steal all their information. Agent Tesla is also delivered through IMG and ZIP files too. Via: BleepingComputer